Building Secure DevOps with Visual Studio Team Services

Last Saturday, on the 21st March 2018, Global Azure Bootcamp 2018 - all user groups and communities came together to deliver content on Azure and Cloud Computing. I delivered one session in Singapore on DevOps with VSTS.
This week, I will share the content on “Building Secure DevOps with VSTS”.
DevOps is the union of PEOPLE, PROCESS and TOOLS to enable the continuous delivery of value to CUSTOMERS. Essentially, DEVelopment and OPerationS. Many a time I hear in multiple conversations asking if they could purchase DevOps or otherwise then install it. The answer is simple - NO. I have to emphasize that you cannot buy DevOps nor install it. Today, I won’t be talking about what DevOps is and what DevOps isn’t, I will dive straight into the “How to build a secure DevOps pipeline with Visual Studio Team Services (VSTS)“
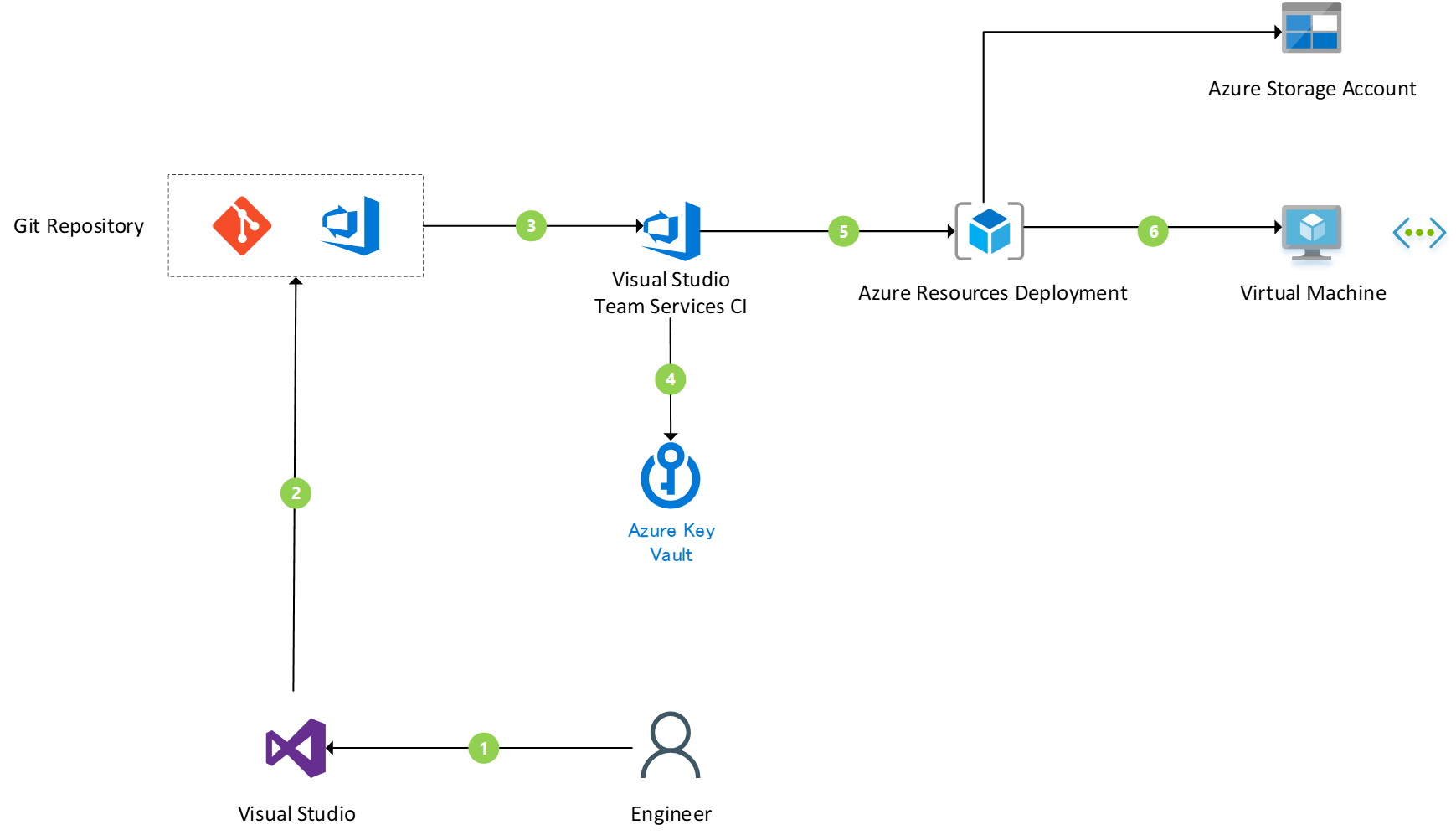
Before we get started, this is the architecture diagram for this demo solution.
Getting Started
Firstly, we’ll start by creating an Azure Key Vault. Azure Key Vault is Azure’s secure key management to store our secret keys in a safe place that promises enhanced data protection and compliance.
Creating Azure Resource
As most Azure resource, we’ll describe our Key Vault with a name, resource group, pricing tier and access policies. The access policies will by default set the current user as the principal user. I will not go deep dive into the configuration of Service Principal for Key Vault since Azure will be added as an authorized endpoint on VSTS, hence, we can skip this step.
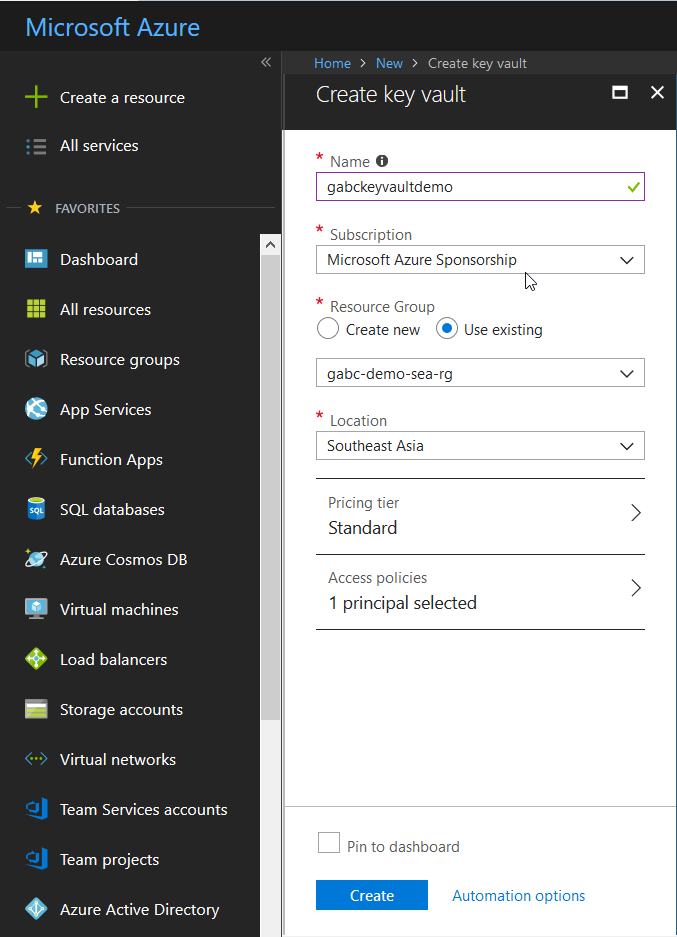
Great! We’ve got our Azure Key Vault resource created, now we’ll “Generate/Import secrets into our Key Vault. This is where we will store our secrets.
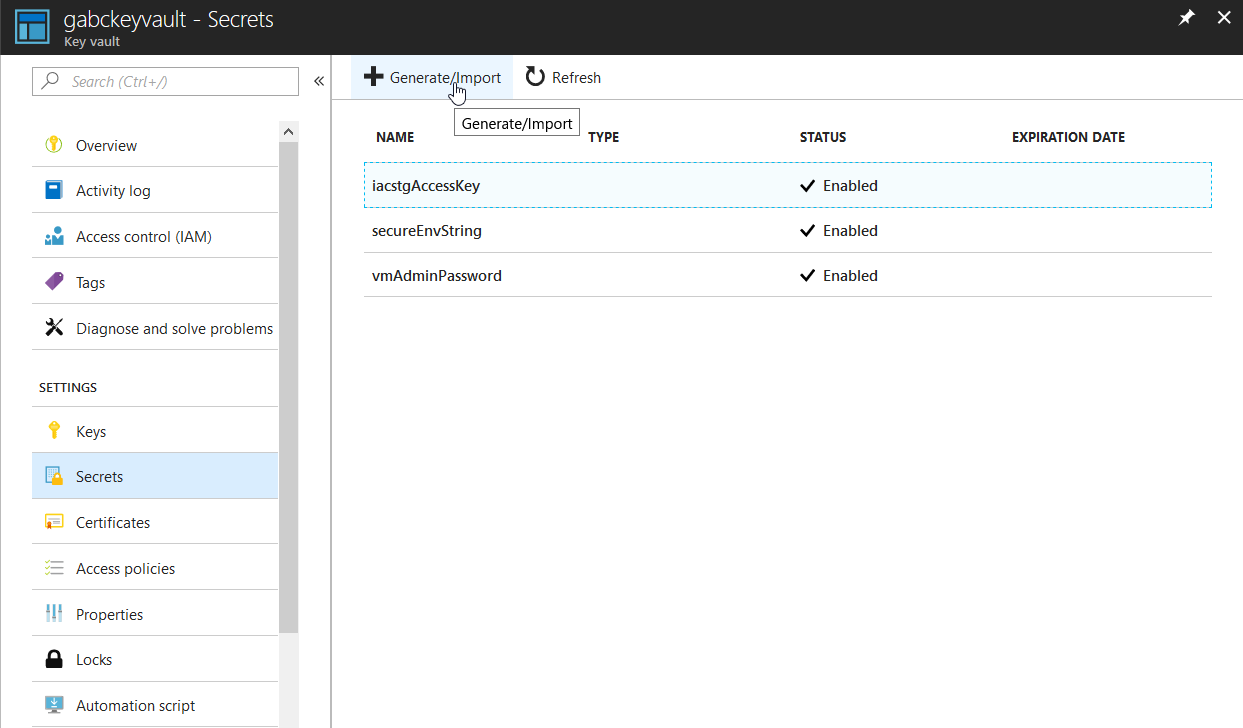
Here, we can manually upload our secret key or to choose to upload a certificate. In this example, we’ll upload a manual secret key. It’s pretty straightforward, the name will be the name that we will reference to later on, while the value holds the secret that we want to store. Of course, we can set when will it be activated and how long the expiration of the key shall survive.
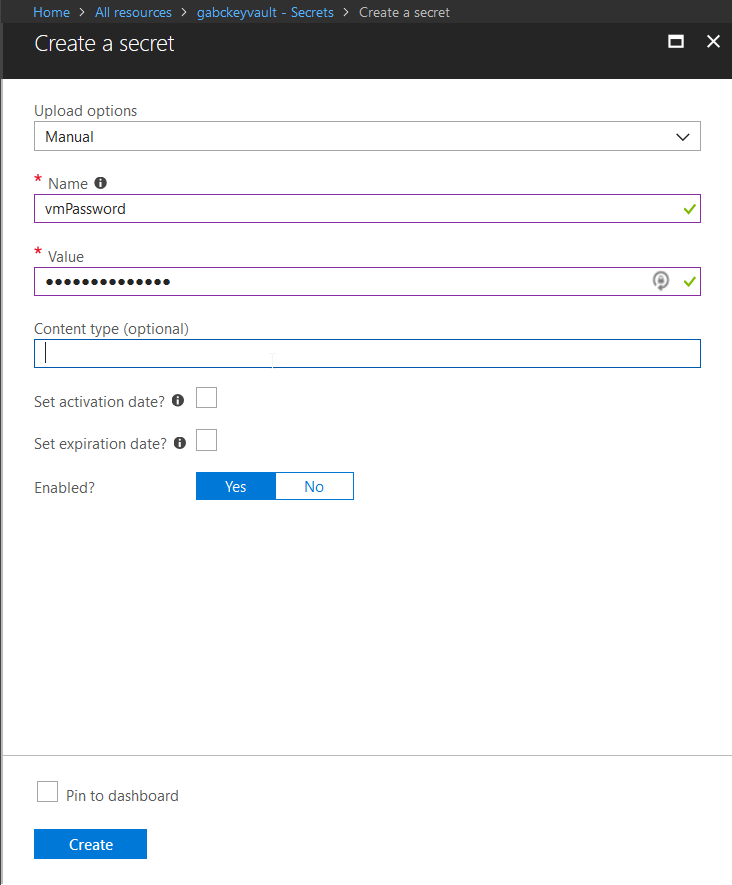
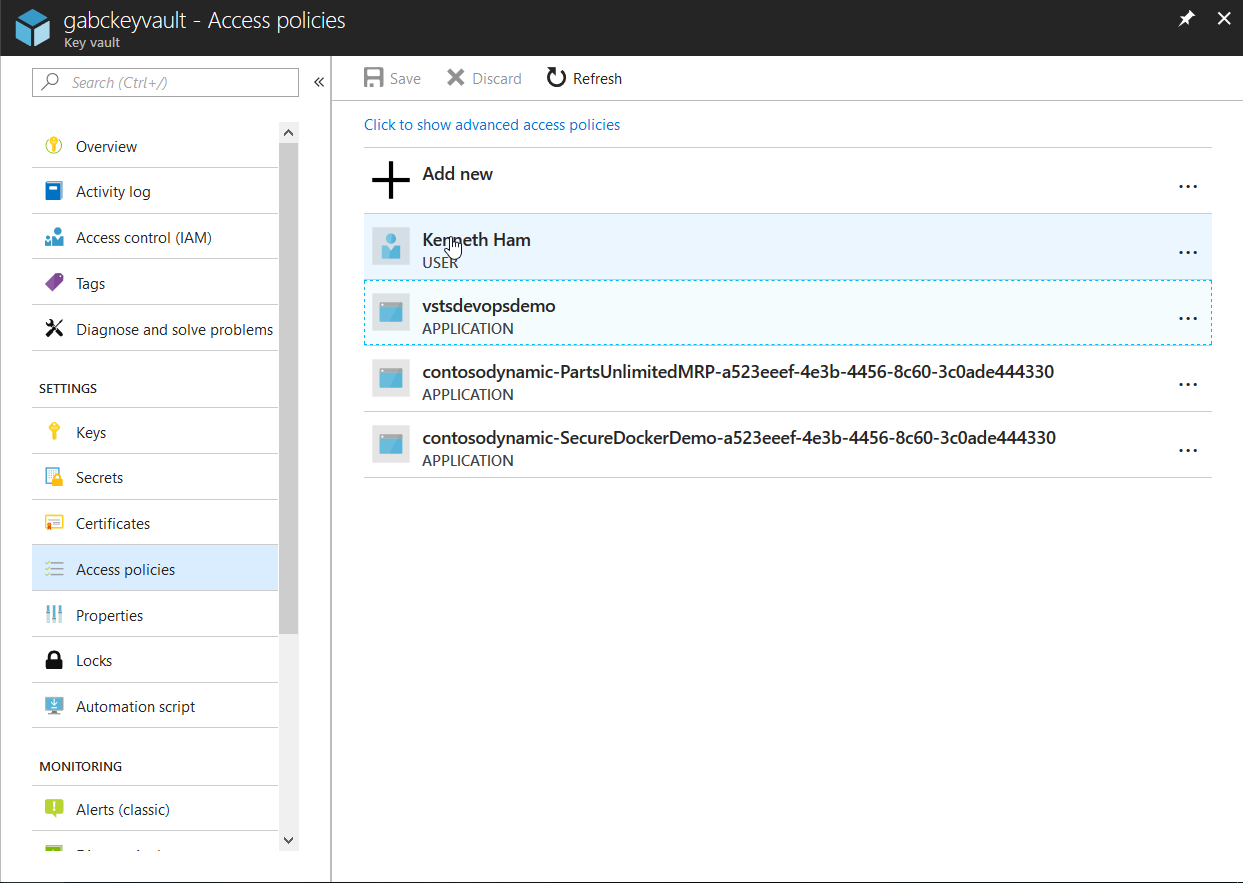
“Access Policies” to set the permissions to which allows your application to access Key Vault. In our case, I’ve set the access policies for myself to Get and List operations to Key Vault.
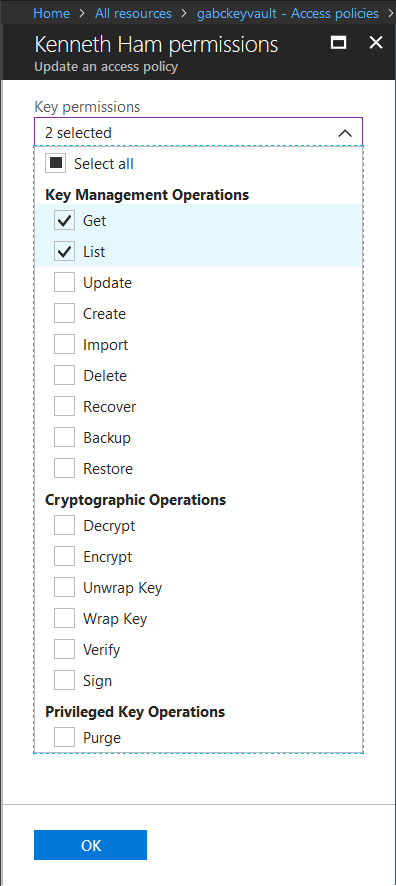
Alright! We’ve got through quite abit to setup Key Vault, now we’ll dive into building Azure Resource Manager (ARM) template on Visual Studio 2017.
Build ARM Template
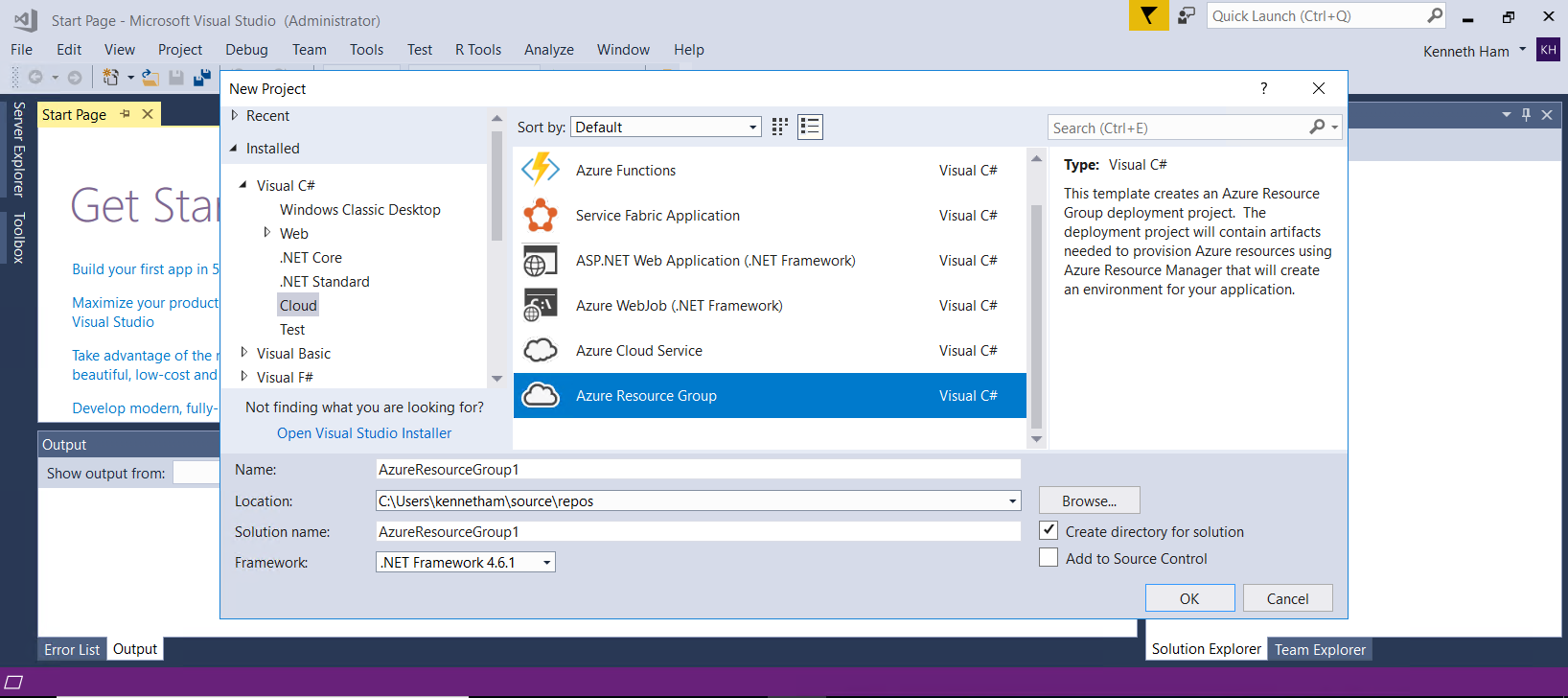
First off, let’s open up our Visual Studio 2017. File -> New Project, let’s create a Azure Resource Group Project under Cloud.
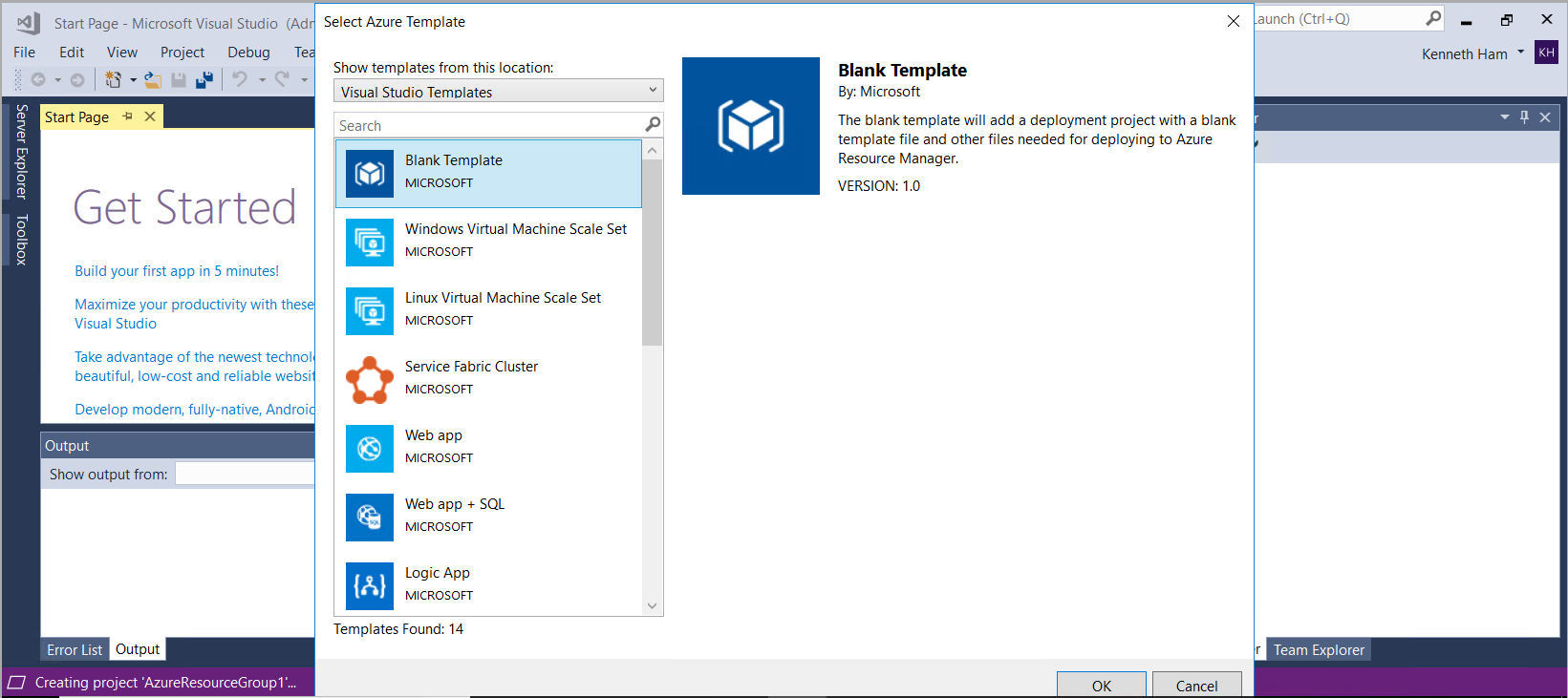
There are many pre-baked templates that you could easily create and deploy. Let’s start with a blank template so we understand the end-to-end development of Infrastructure-as-a-code.
Azure Deploy Configuration
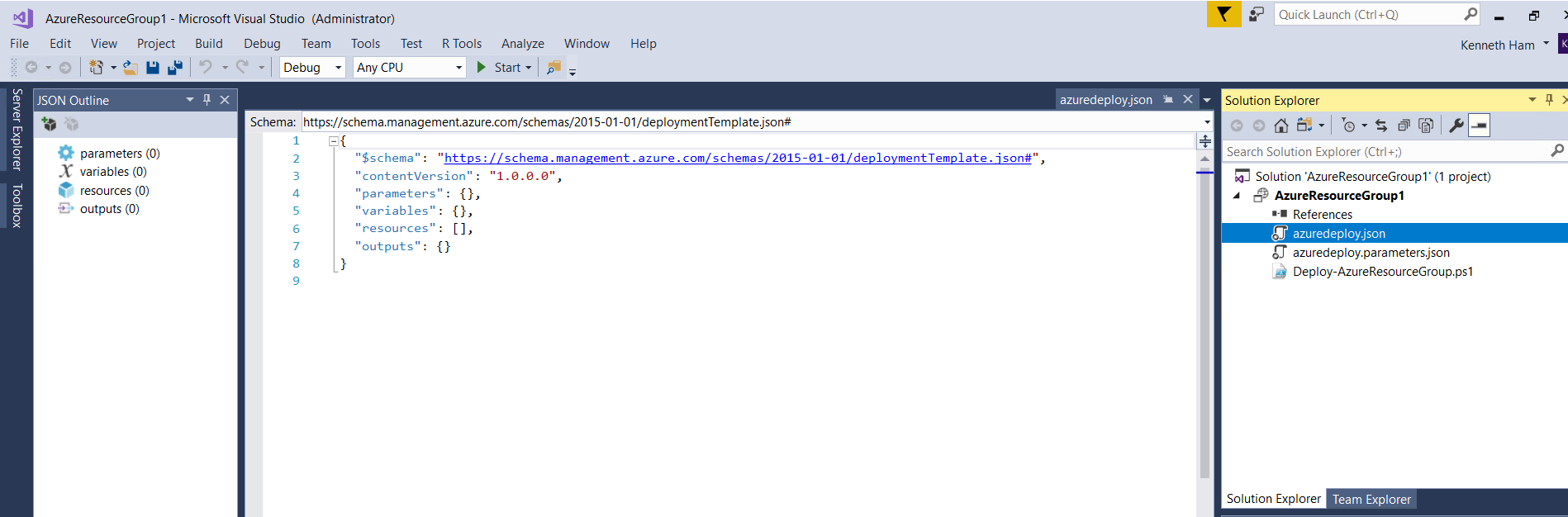
Let’s start by looking at azuredeploy.json. This is a “magical” file that basically automates the deployment process on Azure. By running this file, Azure knows what services it needs to create. From here, we can start adding resources to be deployed. By Double-clicking azuredeploy.json, JSON Outline will be displayed where at one glance, we can see the parameters, variables, resources and outputs of the defined resource group.
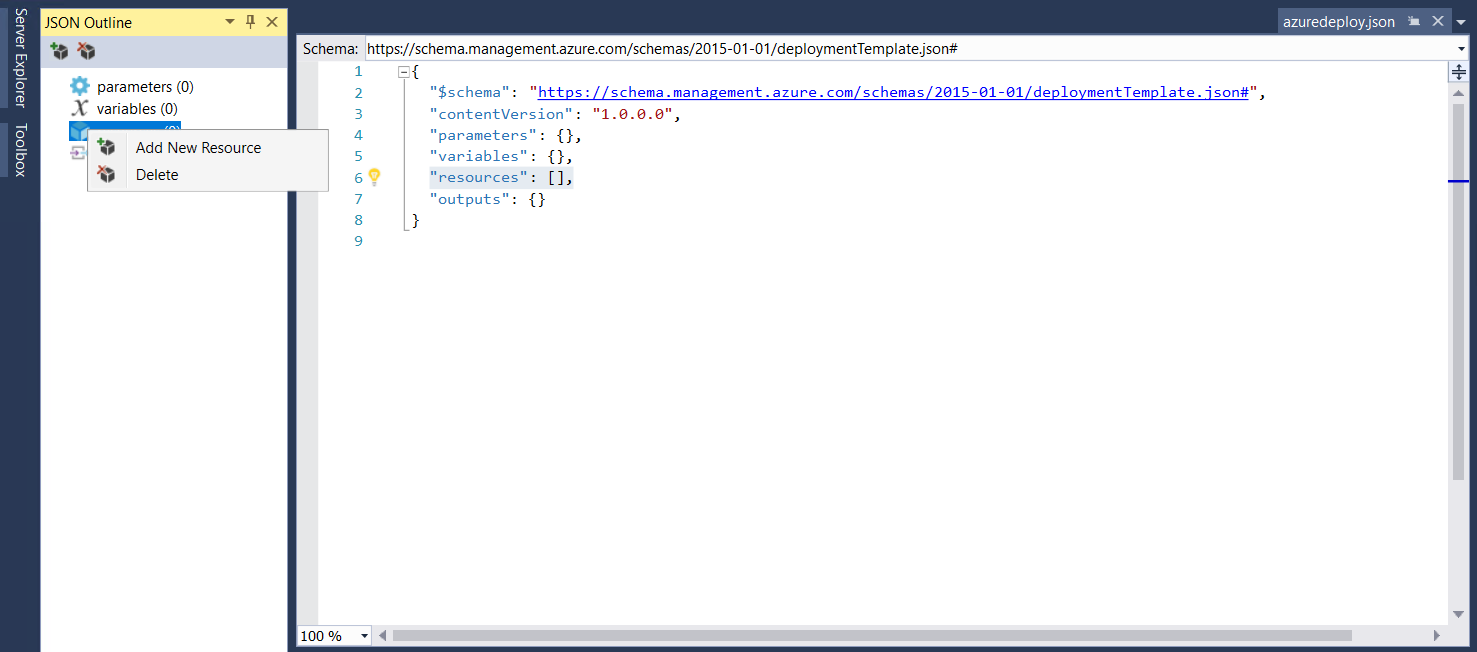
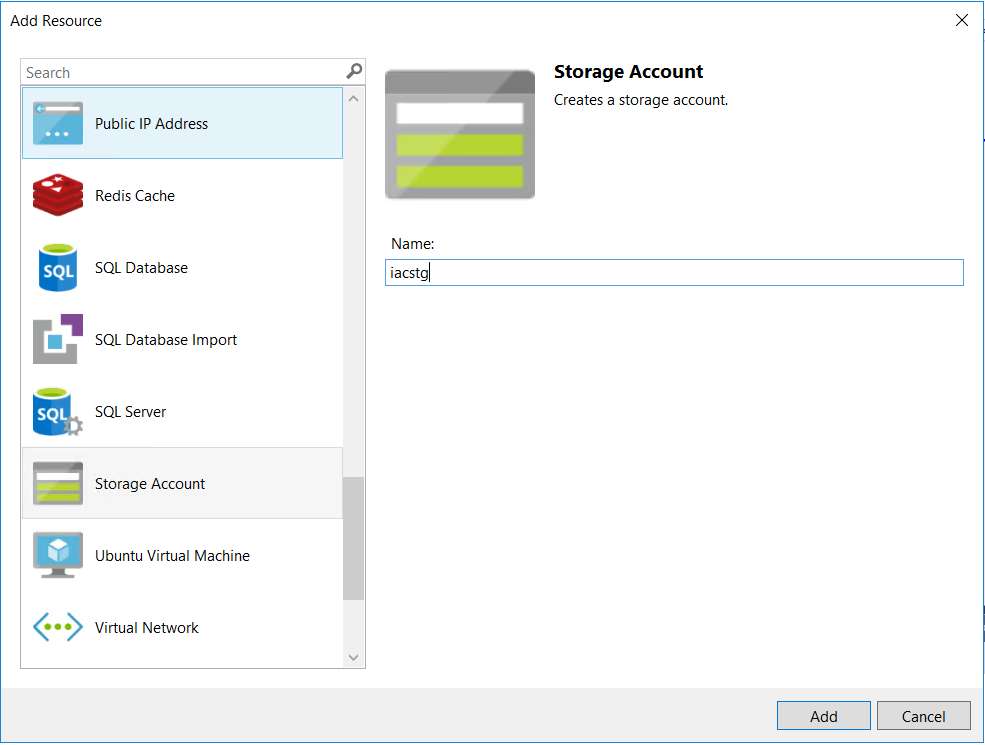
Right-click on “Resources” -> “Add New Resource”. We’ll add a new Storage resource.
Name the storage anything you want, no configuration is required here.
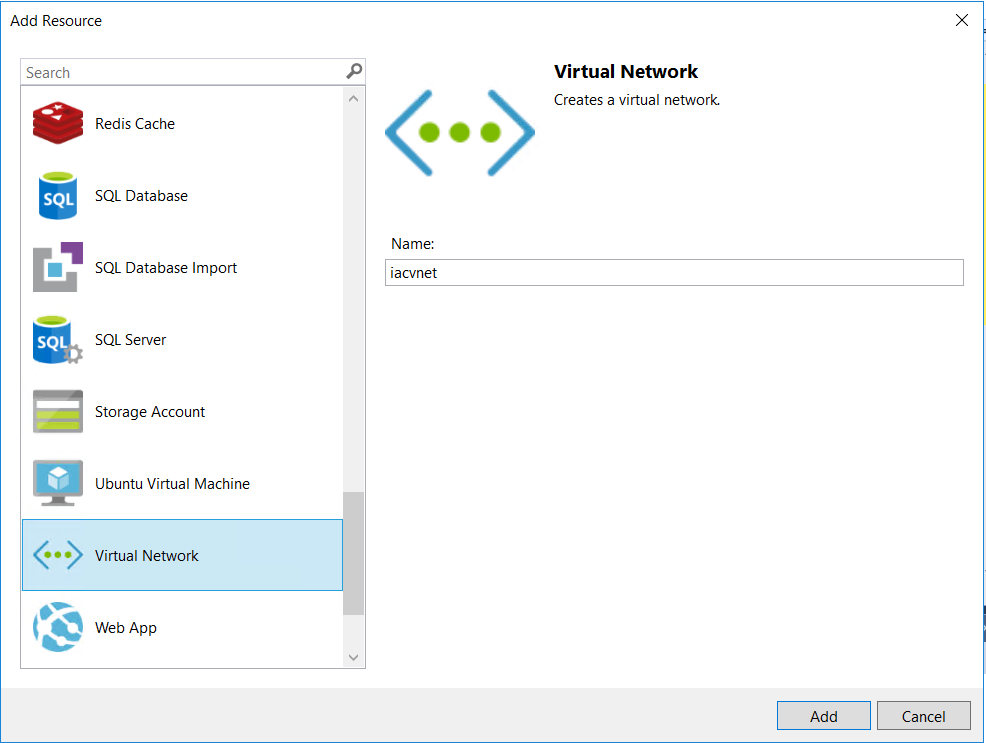
Next, we’ll need to create a virtual network resource. This will define the network subnet address of the virtual machine.
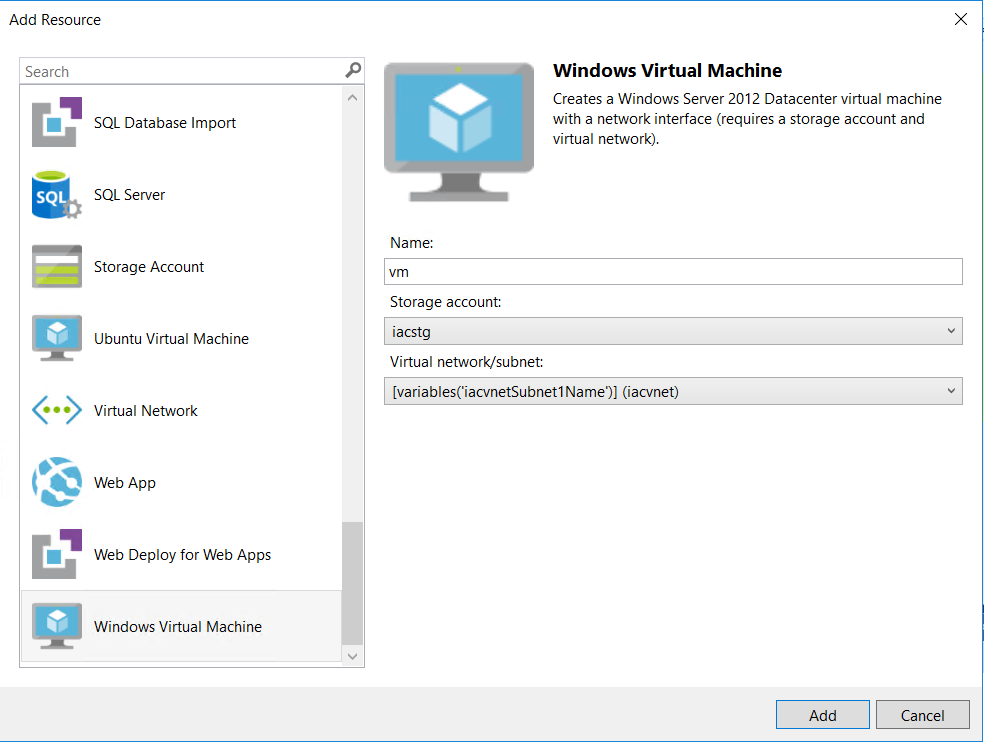
Now, we’ll create a new Virtual Machine resource and set the “Virtual Network/subnet” to subnet1. This will also create a Virtual Network Interface card for us.
Next, we’ll also add a public IP address to be able to communicate outside the network.

Configure VM
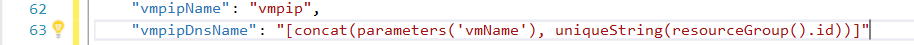
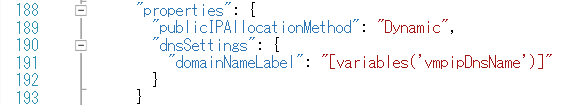
We’re all set with that! Pretty straightforward isn’t it? However, that’s not it. Let’s set the VM DNS name.
Click on “Variables” -> “vmpipDnsName”, then configure the following.
Next, head to “Resources” -> “vmpip” and update the DNS in resources.
Reference Azure Key Vault in ARM Template
Finally, we’ve got this far! The last step is to reference Azure Key Vault secrets within ARM template.
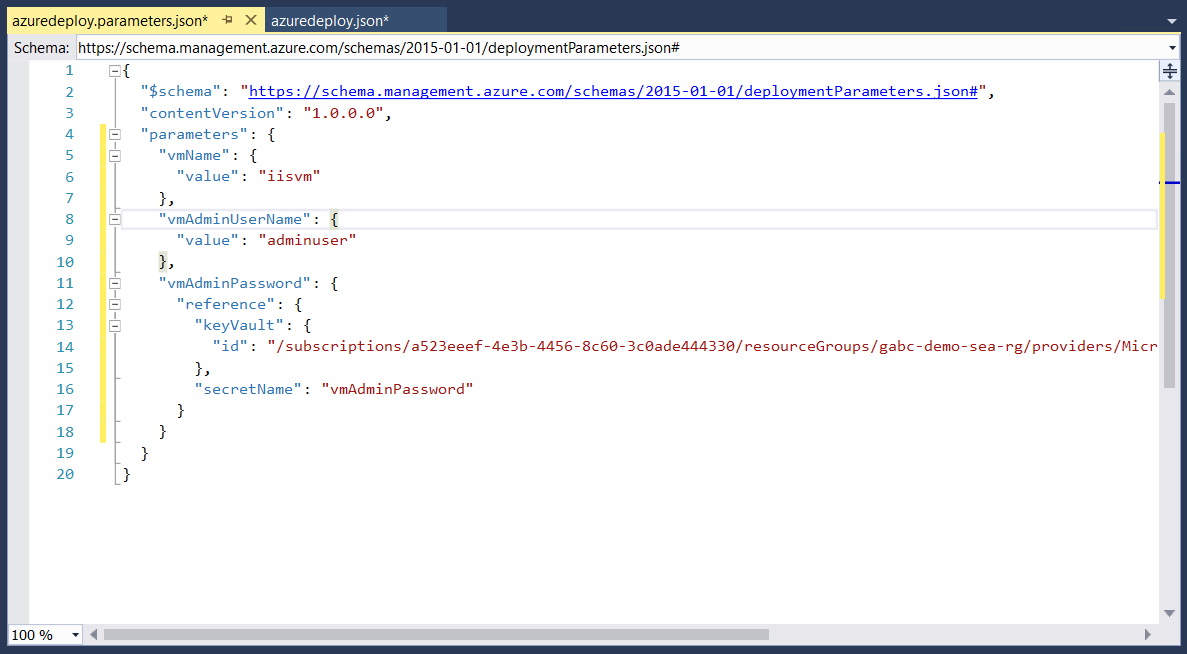
Backend, this is what is happening. The parameter file will reference the secret from Azure Key Vault and passes the secret to ARM template.
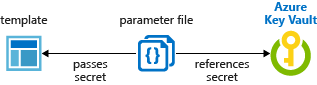
We’re going to create a key vault reference so that this deployment will be secure end-to-end. The idea is to remove any possible leakage of information and/or secrets in our codes. We’re be editing the azuredeploy.parameters.json file. This file holds the parameters required for our Virtual Machine to inherit its username and password. In our scenario, we have referenced Azure Key Vault to our VM Password secret without leaking any sensitive information.
That’s it!
Recap
Let’s recap what we’ve learnt. In this article, I am demonstrating the ability to a secure CI/CD DevOps pipeline with VSTS. We began by introducing the configuration of Azure Key Vault, then developed an ARM template to deploy Azure Resources that creates a reference to secrets managed by Azure Key Vault.
Slide Deck:
Cheers!